Colabora y gana una camiseta de KDE España Akademy-es de Málaga 2023 Opensouthcode Edition
En esta ocasión tengo muy fácil hacer esta entrada ya que básicamente es un copia y pega de la entrada que he hecho para la Asociación en la que anunciamos la iniciativa «Colabora y gana una camiseta de KDE España Akademy-es de Málaga 2023 Opensouthcode Edition». ¿Te interesa? Sigue leyendo.
Colabora y gana una camiseta de KDE España Akademy-es de Málaga 2023 Opensouthcode Edition
Tal y como podemos leer en la página web de KDE España:
¿Quieres ganar una camiseta conmemorativa de la última Akademy-es celebrada en Málaga? Pues lo tienes muy fácil.

Para conseguirla debes realizar alguna de las siguientes acciones:
- Conseguir traer a la asociación un nuevo socio (ver condiciones y proceso en este enlace)
- Resolver un bug de KDE (mira cómo se hace en este artículo)
- Realizar 3 informes de bugs a partir de la publicación de estas bases hasta el lanzamiento de Plasma 6 (que será el 28 de febrero de 2024, mira como se hace en este enlace)
- Escribir 3 artículos de calidad hablando de noticias de KDE en tu blog (más de 300 palabras, que sea original, etc.)
- Poner subtítulos a los vídeos de los podcast largos de KDE España o charlas de Akademy-es. (ponte en contacto con la asociación para conocer detalles )
Bases:
- KDE España se reserva el derecho de dar por válidas las participaciones.
- Para dar fe se debe enviar un correo a junta@kde_espana.org donde se muestre que ha cumplido con los requisitos: capturas de pantalla, bug resuelto, enlaces, etc.
- En caso de que estos sean correctos nos pondremos en contacto contigo para pedirte los datos del envío de la camiseta.
- La promoción es válida hasta agotar existencias.
- Solo se puede ganar una camiseta por persona.
Así que, no te lo pienses más y ponte manos a la obra ya que participando no solo puedes conseguir una camiseta sino que colaboras a que el Software Libre siga creciendo.
¿Qué es Akademy-es?
Akademy-es (#akademyes, que es la etiqueta para las redes sociales) es evento más importante para los desarrolladores y simpatizantes de KDE, que se ha ido celebrando desde el 2006 con éxito creciente.
En general, las Akademy-es son el lugar adecuado para conocer a los desarrolladores, diseñadores, traductores, usuarios y empresas que mueven este gran proyecto.
En ellas se realizan ponencias, se presentan programas, se hace un poco de caja para los proyectos libres (camisetas, chapas, etc) pero sobre todo se conoce a gente muy interesante y se cargan baterías para el futuro.
La entrada Colabora y gana una camiseta de KDE España Akademy-es de Málaga 2023 Opensouthcode Edition se publicó primero en KDE Blog.


Linux Connexion Distros Madres II en Podcast Linux #195
Aunque el proyecto Podcast Linux está parado esto no significa que no tenga cabida en el blog, y mientras pueda seguiré promocionándolo con la esperanza de que reviva, como cierto pájaro mitológico. Bienvenidos a un nuevo audio de Podcast Linux, concretamente el episodio 194 titulado » Linux Connexion Distros Madres II» donde Juan Febles realiza una mesa redonda con tres usuarios de distribuciones demostrando que la variedad en el mundo del Software Libre está garantizada y, en mi opinión, aporta más cosas positivas que negativas.
Linux Connexion Distros Madres II en Podcast Linux #195

Cada cierto tiempo me gusta promocionar los audios de Podcast Linux, un programa de Juan Febles que realizaba con mucho cariño y que siempre teníia cosas interesantes que descubrir.
Como los lectores del blog sabrán hace casi un mes este proyecto cerró sus emisiones por motivos que solo incumben a su creador. Desde el blog no quiero dejar que su recuerdo se desvanezca así que seguiré publicitando sus audios ya que su calidad no debe caer en el olvido.
En esta ocasión Juan Febles toca retoma un tema que ya trató, el de las diferentes distribuciones Linux, siendo este audio la segunda parte de uno que realizó hace unos meses y que llamó «Distros no Debianitas» y del que ya hablé en el blog.
En palabras de Juan:
¡¡¡Muy buenas amante del Software Libre!!!
Bienvenido a otra entrega, la número 195 de Podcast Linux. Un saludo muy fuerte de quien te habla, Juan Febles. Hoy vamos a hablar de Distros Madres con usuarios.
Voro MV , es miembro de GNU/Linux Valencia, bloguero, podcaster, Youtuber y un amante del motociclismo. Desde hace mucho tiempo utiliza Debian GNU/Linux.
Vicfred es Mejicano, trabaja en mountain view California en Google como ingeniero de software. Estudió matemáticas puras. Es el fundador de C++ México, streamea resolviendo problemas de programación en vivo. Ha usado gentoo como su distro principal desde hace 14 años.
Juan Almiñana, más conocido en la Linuxfera como Linuxero Errante, es un apasionado GNU Linux y el Software Libre. En su canal de Youtube habla de GNU/Linux y otros temas que le resulten interesantes, siempre como base el mundo linuxero . Es usuario doméstico de este sistema que tanto le gusta, y la libertad y el buen rollo son dos bases importantes en este camino por el Software Libre. Es usuario de Void Linux.
Recordar a los oyentes que estamos en una sala Jitsi para esta charla, un servicio libre para videoconferencias, y que este podcast se aloja su web en Gitlab, un servicio libre de repositorios git y su contenido en Archive.org, la biblioteca digital libre con licencias Creative Commons.
Enlaces:
- Vídeo instalación Gentoo: https://www.youtube.com/live/B53jJqjwTl4
- Voro MV: https://mastodon.online/@voromv
- Youtube Voro MV: https://www.youtube.com/VOROMV
- Vicfred: https://bsd.network/@Vicfred
- Twitch Vicfred: https://www.twitch.tv/Vicfred
- Linuxero Errante: https://twitter.com/JuanAlGr
- Youtube Linuxero Errante: https://www.youtube.com/c/JuanJJLinuxeroerrante
Así que os invito a escuchar este mesa redonda donde se muestran la variedad del Software Libre.
Más información: Podcast Linux
Sigue a Podcast Linux
Aprovecho para animaros a seguir Podcast Linux en algunos de los canales de comunicación que tiene:
- Twitter: https://twitter.com/podcastlinux
- Mastodon: https://mastodon.social/@podcastlinux/
- Correo: podcastlinux@disroot.org
- Web: https://podcastlinux.com/
- Telegram: https://t.me/podcastlinux
- Telegram Juan Febles: https://t.me/juanfebles
- Youtube: https://www.youtube.com/PodcastLinux
- Feed Podcast Linux: https://podcastlinux.com/feed
- Feed Linux Express (Audios Telegram): https://podcastlinux.com/Linux-Express/feed
La entrada Linux Connexion Distros Madres II en Podcast Linux #195 se publicó primero en KDE Blog.

Qué son esas pantallas que vemos en NeoMutt
Echemos un vistazo a qué es es cada menú y pantalla que se nos muestra en NeoMutt, el cliente de correo para la terminal

Cuando abrimos NeoMutt por primera vez, nos encontramos unas cuantas ventanas y apartados que conforman este cliente de correo para la terminal. Vamos a hacer un repaso de qué es cada uno y qué función desempeña.
Este artículo es una nueva entrega de los artículos relacionados sobre NeoMutt que he publicado en mi blog, a la vez que poco a poco voy adentrándome en el uso de este cliente de correo.
Índice
El índice es la pantalla que normalmente ves en primer lugar cuando inicias NeoMutt. Ofrece una descripción general de tus correos electrónicos en el buzón abierto actualmente.
De forma predeterminada, este es el buzón de tu sistema. La información que ves en el índice es una lista de correos electrónicos, cada uno con su número a la izquierda, sus banderas (correo electrónico nuevo, correo electrónico importante, correo electrónico que ha sido reenviado o respondido, correo electrónico etiquetado,…), la fecha en la que se envió el correo electrónico, su remitente, el tamaño del correo electrónico y el asunto.
Además, el índice también muestra jerarquías de hilos: cuando respondes a un correo electrónico y la otra persona responde, puedes ver el correo electrónico de la otra persona en un «subárbol» a continuación.
Esto es especialmente útil para el correo electrónico personal entre un grupo de personas o cuando te has suscrito a listas de correo.
Paginador
El paginador es el responsable de mostrar el contenido del correo electrónico. En la parte superior del paginador, aparece una descripción general de los encabezados del correo electrónico más importantes, como el remitente, el destinatario, el asunto y mucha más información.
La cantidad de información que se muestra se puede configurar en los archivos de configuración ajustando las variables necesarias a los parámetros que se desean.
Debajo de los encabezados, verás el cuerpo del correo electrónico que normalmente contiene el mensaje.
Si el correo electrónico contiene archivos adjuntos, verás más información sobre ellos debajo del cuerpo del correo electrónico o, si los archivos adjuntos son archivos de texto, podrás verlos directamente en el paginador.
Para que el paginador muestre el texto de una manera más amigable, se puede configurar para que muestre los distintos textos en diferentes colores. Se puede configurar un color distinto para cada cosa: el texto citado, direcciones de correo, URL, etc.
La barra lateral
La barra lateral muestra una lista de todos tus buzones o carpetas que tengas configuradas en tu cuenta de correo. La barra se puede activar y desactivar, puede tener un tema de color y se puede configurar el estilo en el que se muestran los elementos de la lista.
Todo lo que se muestra en el panel es configurable: si se muestra o no la barra lateral, el ancho de la barra, las carpetas que deseamos que se muestren, los colores, etc.
Estas son a grandes rasgos, las pantallas que vemos primero al ejecutar NeoMutt. Para movernos por ellas, deberemos utilizar los atajos de teclado propios del propio NeoMutt o los que hayamos configurado nosotros mismos según nuestros gustos.



スクリーンロックが固まったときは?
この投稿は openSUSE Advent Calendar の 11日目です。そろそろ折返しです。
まれにスクリーンロックが固まってしまい、パスワードの入力画面が表示されいことがあります。このようなときに、ロックを解除する方法があります。使用するのは systemd に含まれているコマンド、loginctl です。
ロック画面が固まってしまったら、まず行うのが仮想コンソールでのログインです。Ctrl+Alt+F1を押すとログインプロンプトが表示されるので、ユーザー名とパスワードを入力してログインしてください。
つぎに、loginctl を実行すると、セッションの一覧が表示されます。
$ loginctl
SESSION UID USER SEAT TTY
22 1000 geeko seat0 tty1
3 1000 geeko seat0
2 sessions listed.セッション 22 は、TTY が tty1 なので、現在操作している仮想コンソールです。固まっているのはセッション 3 です。
ロックを解除するには、以下のコマンドを実行します:
$ loginctl unlock-session 3これでロックが解除できました。操作している仮想コンソールを Ctrl+D で抜けて、Ctrl+Alt+F7 を押すと、デスクトップに戻ることができます。


Severe Service Degradation: OBS Unavailable


Post-mortem: Backend Overload


Linux Foundationのレポートが続々日本語化
openSUSEに直接関係は無いのですが、オープンソース関係ということで一ネタ投稿させて頂きます。
Linux Foundationは数多くのレポートを出しています。OSPOについてや、Kubenetesの現状、日本でのオープンソースの展開状況など、とても興味深く面白いレポートばかりです。ですが、英語で出版されているため、なかなか日本語圏の私達には疎遠になりがち、、、、だったのですが、ここの所、続々と日本語版が出版されています。
日本語版は日本語版Linux Foundationの出版物のサイトからダウンロード可能です。
いくつかピックアップしてみますと、
Japan Spotlight 2023
日本でのオープンソースの展開状況について調査結果の数値に基づいた考察をしています。
オープンソースメンテナーズ
有名なオープンソースのメンテナーについて、その現状、課題、ベストプラクティスなどが書かれています。オープンソースのメンテナンスに関わる人必見のレポートです。コミュニティのマネジメントにも有用な内容が沢山です。
Kubernetesプロジェクトジャーニーレポート
Kubernetesのコントリビュートや教育、イベントなどについての数値や考察が書かれています。
その他、LF Energy(エネルギー)関連や、AkrainoなどLF Edge関連のレポートなど、多岐に渡っています。ちょっと眺めてみるだけでもかなり面白いです。


Γνωριμία με το Open Build Service
Το Open Build Service παρέχει ένα ολοκληρωμένο περιβάλλον για την κατασκευή πακέτων λογισμικού για πολλές διανομές Linux, όπως το openSUSE, το Fedora, το Debian, το Ubuntu και πολλές άλλες. Επιπλέον, υποστηρίζει τη δημιουργία πακέτων για αρχιτεκτονικές διαφορετικές από το x86, όπως ARM και PowerPC. Με το OBS, οι προγραμματιστές μπορούν να ανεβάζουν τον κώδικά τους, να ορίζουν τις απαιτούμενες εξαρτήσεις και να δημιουργούν αυτόματα πακέτα λογισμικού για πολλές πλατφόρμες και διανομές.
Τα πλεονεκτήματα του Open Build Service είναι πολλά. Πρώτον, παρέχει μια ενοποιημένη πλατφόρμα για τη δημιουργία πακέτων λογισμικού για πολλαπλές διανομές, εξοικονομώντας χρόνο και πόρους στους προγραμματιστές. Δεύτερον, προσφέρει αυτοματοποιημένες διαδικασίες για τη δημιουργία και την ενημέρωση των πακέτων, προσφέροντας ένα σταθερό και επαναληπτικό περιβάλλον. Τέλος, παρέχει ευέλικτες δυνατότητες προσαρμογής και διαμόρφωσης, επιτρέποντας στους χρήστες να προσαρμόσουν τις διαδικασίες κατασκευής και να προσθέσουν πρόσθετες λειτουργίες ανάλογα με τις ανάγκες τους.
Παρά τα πλεονεκτήματα του Open Build Service, υπάρχουν και μειονεκτήματα που πρέπει να ληφθούν υπόψη. Πρώτον, η εκμάθηση και η εξοικείωση με το σύστημα μπορεί να απαιτήσει χρόνο και προσπάθεια, ειδικά για νέους χρήστες. Δεύτερον, η συντήρηση και η διαχείριση των υποδομών του OBS μπορεί να απαιτήσει επιπλέον πόρους και επιδεξιότητες. Αυτό μπορεί να το παρέχει το openSUSE στην ιστοσελίδα https://build.opensuse.org/.
Χρήστες του Open Build Service
Όσον αφορά στους χρήστες του Open Build Service, αυτοί κυμαίνονται από ανεξάρτητους προγραμματιστές μέχρι μεγάλες επιχειρήσεις. Οι προγραμματιστές μπορούν να αξιοποιήσουν το OBS για να διευκολύνουν τη διαδικασία της κατασκευής, της δοκιμής και της διανομής του λογισμικού τους σε πολλές πλατφόρμες και διανομές. Από την άλλη πλευρά, οι μεγάλες επιχειρήσεις μπορούν να αξιοποιήσουν το OBS για τη δημιουργία ενός ενοποιημένου κέντρου κατασκευής λογισμικού, που επιτρέπει τον έλεγχο και τη διαχείριση των πακέτων σε διάφορες διανομές και πλατφόρμες.Όσον αφορά στον τρόπο χρήσης του Open Build Service, οι χρήστες μπορούν να ανεβάζουν τον κώδικα τους στο σύστημα στην ιστοσελίδα https://build.opensuse.org/ και να ορίζουν τις απαιτούμενες εξαρτήσεις για την κατασκευή του πακέτου. Στη συνέχεια, μπορούν να εκκινήσουν τη διαδικασία κατασκευής, η οποία περιλαμβάνει τη συγκέντρωση και τη σύνθεση των απαιτούμενων στοιχείων για την παραγωγή του τελικού πακέτου με τη χρήση ενός αρχείο spec. Οι χρήστες μπορούν να διαμορφώσουν τις διαδικασίες κατασκευής, να προσθέσουν πρόσθετες ενέργειες και να διαχειριστούν τις εξαρτήσεις τους. Τέλος, το OBS παρέχει διάφορα εργαλεία και δυνατότητες για την αυτοματοποίηση της διαδικασίας κατασκευής, τη διαχείριση των πακέτων και την ενημέρωση του λογισμικού.
Συνοψίζοντας, το Open Build Service είναι μια πλατφόρμα λογισμικού ανοιχτού κώδικα που προορίζεται για τη δημιουργία και την αυτοματοποίηση της διαδικασίας κατασκευής πακέτων λογισμικού. Παρέχει πλεονεκτήματα, όπως την υποστήριξη πολλαπλών διανομών και αρχιτεκτονικών, την αυτοματοποίηση και την προσαρμοστικότητα. Χρησιμοποιείται από προγραμματιστές και επιχειρήσεις για τη δημιουργία και τη διαχείριση πακέτων λογισμικού σε διάφορες πλατφόρμες και διανομές. Με τη βοήθεια του OBS, οι χρήστες μπορούν να αυτοματοποιήσουν και να διαχειριστούν τη διαδικασία κατασκευής πακέτων λογισμικού.


Reloj gigante para tu escritorio, Big Clock – Plasmoides de KDE (235)
Sigo con estas pequeñas aplicaciones que se conocen como applets, widgets o plasmoides y que dotan de funcionalidades de todo tipo a nuestro entorno de trabajo KDE y que parece que van a sufrir un lavado de cara considerable en Plasma 6. Hoy toca un plasmoide sencillo y extremadamente grande, se trata de Big Clock, otro reloj para tu fondo de pantalla que destacas por ser nada sutil. Con este ya serán 235 los elementos de esta serie presentados en el blog.
Reloj gigante para tu escritorio, Big Clock – Plasmoides de KDE (235)
Como he comentado en otras ocasiones, de plasmoides tenemos de todo tipo funcionales, de configuración, de comportamiento, de decoración o, como no podía ser de otra forma, de información sobre nuestro sistema como puede ser el uso de disco duro, o de memoria RAM, la temperatura o la carga de uso de nuestras CPUs.
En esta caso vuelvo uno de los clásicos, los relojes, que gracias al prolífico Zayronxyo están siendo protagonista de esta sección desde hace varias publicaciones. Se trata de Big Clock, que nos muestra de una forma sencilla la fecha y la hora de forma completamente escrita, sin utilizar nada más que letras.
Otra maravilla visual minimalista que creo que aparecerá en mi próximo Viernes de Escritorio y que en su última actualización ha adquirido la posibilidad de cambiar el tamaño de forma sencilla.

Y como siempre digo, si os gusta el plasmoide podéis «pagarlo» de muchas formas en la nueva página de KDE Store, que estoy seguro que el desarrollador lo agradecer?: puntúale positivamente, hazle un comentario en la página o realiza una donación. Ayudar al desarrollo del Software Libre también se hace simplemente dando las gracias, ayuda mucho más de lo que os podéis imaginar, recordad la campaña I love Free Software Day de la Free Software Foundation donde se nos recordaba esta forma tan sencilla de colaborar con el gran proyecto del Software Libre y que en el blog dedicamos un artículo.
Más información: KDE Store
¿Qué son los plasmoides?
Para los no iniciados en el blog, quizás la palabra plasmoide le suene un poco rara pero no es mas que el nombre que reciben los widgets para el escritorio Plasma de KDE.
En otras palabras, los plasmoides no son más que pequeñas aplicaciones que puestas sobre el escritorio o sobre una de las barras de tareas del mismo aumentan las funcionalidades del mismo o simplemente lo decoran.
La entrada Reloj gigante para tu escritorio, Big Clock – Plasmoides de KDE (235) se publicó primero en KDE Blog.


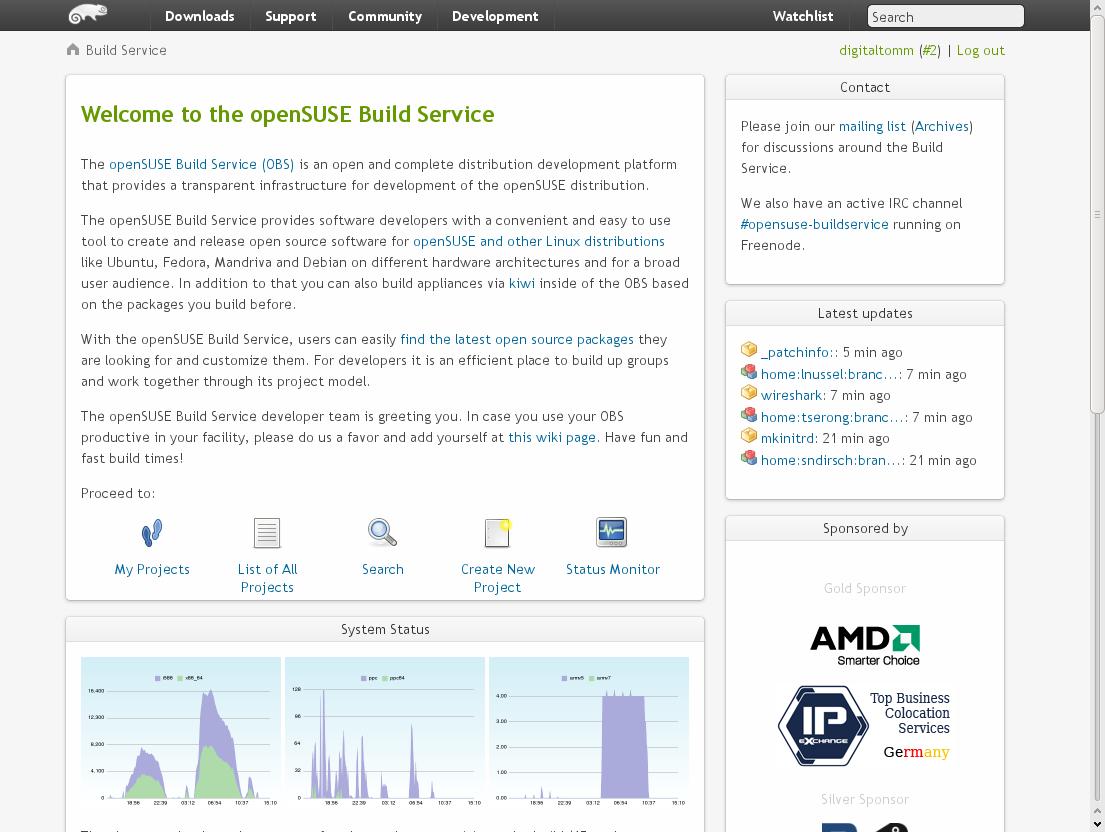
alpで動かしたcockpitを眺めてみる
ALP (Adaptive Linux Platform)は、SUSEとopenSUSEで開発している次世代OSのベースです。イミュータブルで軽量な仕様となっています。
この冬発売のGeeko MagazineにインストールとCockpitというブラウザから管理できるアプリの体験記を書いていますので、ぜひ皆さん試してみてください。
さて、今日はCockpitの「概要」というメニューを見てみたいと思います。
トップ画面です。システム情報、使用率などが表示されてます。
画面にある「メトリックスおよび履歴の表示」のような青い文字の所は、クリックすればメニューが出たりその画面に移動したりします。
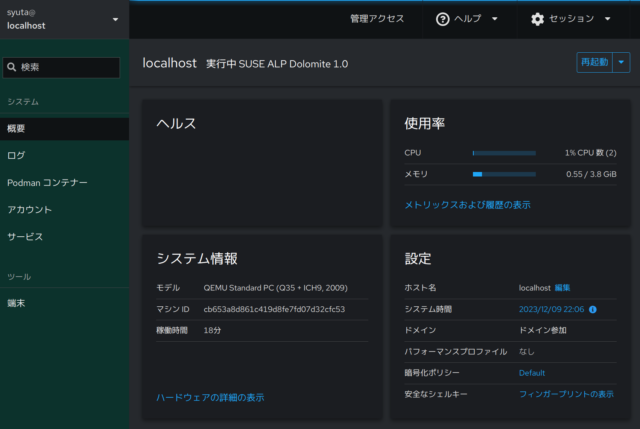
ためしに、「メトリックスおよび履歴の表示」をクリックしてみます。
CPUやメモリなどが表示される画面に移動します。下に「メトリックス履歴に、パッケージcockpit-pcpがありません」と表示がありますが、今の私の環境ではcockpit-pcpというパッケージを見つけられませんでした。
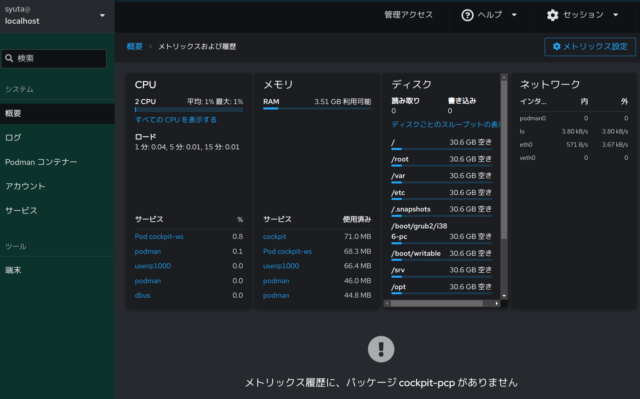
メニューの所にある「ハードウェアの詳細の表示」をクリックしてみます。
下の方にはメモリも表示されてました。色々と設定が表示されています。
メニューの所にある「ホスト名」の右にある「編集」をクリックしてみます。
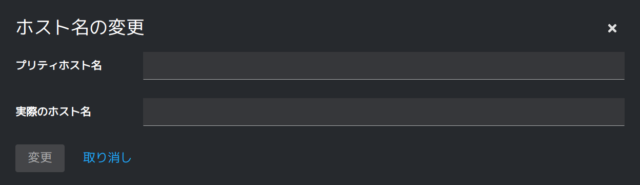
変更画面が出てきました。ここで設定することで、alpのホスト名を変更することができました。
閲覧、変更、と、色々と管理できるようです。別のメニューもどんどん見ていきたいと思います。
 Member
Member baltolkien
baltolkien